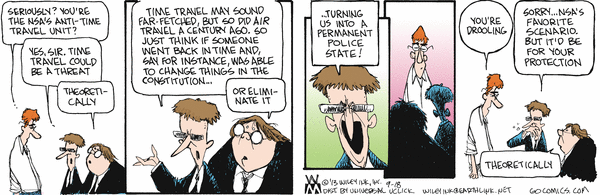
Steve Benson - Gun Grabber
While Steve Benson may have his act together when it comes to realizing that God is a bunch of superstitious nonsense he still has to figure out that guns are the solution to the problem of government. In this cartoon Steve Benson shows he is a gun grabber.
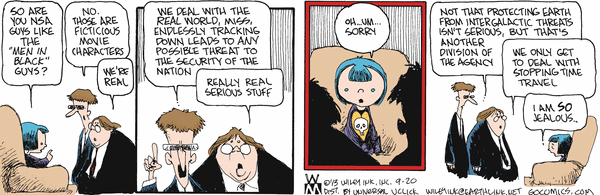
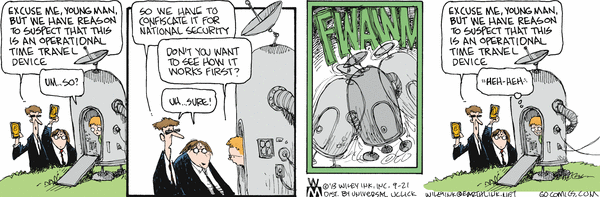
Non Sequitur - Danae & Jeffery get Pinged by NSA thugs????
Use to make a web page on this photos


Arizona DUI tests are no longer required by law!!!!!!!
Arizona Mandatory DUI Breathalyzer tests ruled unconstitutional - Don't take the !!!!

Arizona Mandatory DUI tests unconstitutional????
SourceArizona Supreme Court bars DUI blood tests without warrant
HOWARD FISCHER Capitol Media Services
PHOENIX -- Police cannot use the state's traffic laws to draw blood from suspected drunk drivers without a warrant absent their specific permission at the time of the test, the Arizona Supreme Court ruled Thursday.
In a unanimous decision, the justices rejected the contention by the Pima County Attorney's Office that all Arizona motorists give "implied consent" to having blood, breath or urine tests as a condition to be licensed to drive. They said that means, absent a clear -- and voluntary -- consent immediately prior to the blood draw, it is an illegal search without a warrant.
In a wide-ranging ruling, the high court also said that the ability of juveniles to give that voluntary consent is not absolute -- and not the same as an adult. Justice Scott Bales, writing for the court, said a trial judge must consider all the factors, including the age of the suspect and the failure to notify parents.
But the justices refused to rule that the absence of a juvenile's parents automatically means any consent is not voluntary.
Thursday's ruling most immediately means that charges of driving under the influence of drugs will be dropped against the youth, identified in court records only as Tyler B. because he was 16 at the time of the arrest.
But he is not out of the legal woods yet. Deputy County Attorney Nicolette Kneut said Tyler, who has since turned 18, still faces charges of possession of marijuana and possession of drug paraphernalia in justice court as an adult.
Pima County Attorney Barbara LaWall said Thursday's ruling will complicate the job that police statewide are required to do. She said the high court has provided no guidance.
"How is the officer supposed to know whether or not it's been an express consent," she said. "It just makes it really, really tough because there isn't any bright line." [Duh, the 4th Amendment you idiot!!!!]
LaWall said the ruling means that her office will advise police to get a court-ordered warrant whenever possible before drawing blood, even when a motorist -- and now, especially a juvenile -- gives approval for a blood draw. That, she said, eliminates any possibility of having that consent later ruled involuntary.
According to court records, Tyler and two friends arrived late to school. A school monitor smelled marijuana on the boys and also saw drug paraphernalia in Tyler's car.
The boys were detained in separate rooms while sheriff's deputies were contacted.
A deputy read Tyler his Miranda warnings against self-incrimination and the right to an attorney. But the court files said that Tyler, in the presence of several school officials, admitted he had driven his car to school after smoking marijuana and that he owned some of the paraphernalia in the car.
When the deputy placed Tyler under arrested, the youth became agitated and was placed in handcuffs while the deputy retrieved a blood-draw kit from his car.
On returning, he saw Tyler had calmed down and he removed the cuffs. He then read Tyler from the law which says that Arizona motorists must consent to blood or other tests and that refusal will result in automatic suspension of driving privileges.
Tyler agreed verbally and in writing to the blood draw. But when the case went to court, Tyler argued his consent was not voluntary and that, as a minor, he lacked capacity to consent.
When the court commissioner agreed and suppressed the evidence, the Supreme Court agreed to hear the case. Bales said the issue has never been decided in Arizona.
Bales rejected arguments by prosecutors that "implied consent" law means there is no need to determine whether a consent at the time of the blood draw is voluntary.
"A compelled blood draw, even when administered pursuant to (the implied consent law) is a search subject to the Fourth Amendment's constraints," he wrote for the court. "Such an invasion of bodily integrity implicates an individual's most personal and deep-rooted expectations of privacy."
He said the law says only that an officer must ask a suspect to submit to the test -- and that if a person refuses, a warrant is needed and the suspect's licenses is suspended.
Bales said a motorist can allow a warrantless search "provided the consent is voluntary." But that, he said has to be decided by a court based on all the circumstances, including the suspect's age -- and even whether a parent is present.
In this case, Bales wrote, the court commissioner was correct in ruling that, based on the evidence she had, Tyler's consent was not voluntary.
He said Tyler was detained for about two hours in a room in the presence of school officials and a deputy, without his parents.
"Tyler initially was shaking and visibly nervous," Bales wrote, and placed in handcuffs until he calmed down. And he said that the law read to him about "implied consent" ended with the statement, "You are, therefore, required to submit to the specified tests."
It was only then, Bales said, Tyler consented to the blood draw.
Thursday's ruling drew a special comment from Justice John Pelander. He said his own review of the evidence leads him to believe Tyler did voluntarily consent.
But Pelander said Arizona law requires he and the other justices not to reweigh the evidence but only to consider whether the court commissioner abused her discretion in suppressing the evidence.
But of course don't expect anything to happen, other then hear a bunch of hot air from the members of the Congress and Senate who will be promising to end all these crimes if they just get reelected.
Reach Robert Robb at robert.robb@arizonarepublic.com or 602-444-8472.
Posted on September 26, 2013 4:28 pm by Robert Robb
Put NSA in a narrower box
The United States needs to put the National Security Agency into a much more narrowly defined box. It’s out of control. And it’s out of control in a way that violates civil liberties and harms U.S. national interests.
Brazil is Latin America’s leading economy and one of the most important countries in the developing world. The United States wants warmer relations with it and to facilitate that had invited President Dilma Rousseff for a rare full-spectrum state visit, with all the pomp and circumstance such occasions can be vested with. For U.S. diplomacy, it was a big deal.
Rousseff canceled the state visit. She did, however, come to the United States. She went to the United Nations to harshly denounce the United States.
Why? News came out that the NSA was intercepting her phone calls and emails. And those of her staff and government. And of Petrobras, the Brazilian state oil company.
The National Security Agency is supposed to be a “security” agency. It is part of the Department of Defense.
So, what threat to U.S. security do the Brazilian president, her government and the state oil company pose?
Earlier it was revealed that the NSA was extensively snooping on European Union officials. And what threat to U.S. national security were they hatching?
The NSA was looking at the emails of Mexican President Enrique Pena Nieto – before he was ever elected.
This gratuitous spying, with utterly no rational connection to protecting the United States against any conceivable security threat, has consequences.
Obviously, it put the kibosh on an important U.S. diplomatic overture to Brazil, to put it mildly.
Brazil is in the market for some new fighter jets. Boeing, a U.S. company, is a bidder. The NSA making sure there are no terrorist plots emanating from Rousseff’s office is thought to have damaged its prospects.
Brazil is also auctioning off deep-sea oil concessions, in which American companies have an interest. In Brazil, however, the question is whether NSA spying on Petrobras has irredeemably tainted the process.
The United States wants a free trade agreement with the European Union. NSA spying on EU officials has, unsurprisingly, cooled interest in Europe and raised questions about whether the integrity of negotiations for such a treaty could be protected.
Domestically, NSA is also out of the box. It’s not supposed to be prying within the United States. The Patriot Act increased the intelligence gathering power of the FBI, not the NSA. Yet it is the NSA that has the telephone records of virtually every U.S. resident.
The NSA has an important job to do. It’s supposed to gather intelligence about true national security threats. In so doing, it will need periodically to follow leads to sources in this country and in foreign governments.
But that’s not what the NSA is doing. Its indiscriminate collection of data is vastly outside its writ, violates civil liberties domestically and internationally, and is damaging U.S. interests.
It is also jeopardizing NSA’s ability to do its true national security job. NSA can tap so easily into Internet data because so much of it is routed through the United States. The NSA revelations, however, have caused other countries to become more interested in developing Internet routes that avoid the United States. They have also given impetus to calls to put the Internet under some sort of international control, which would be disastrous in numerous respects.
Yes, everyone spies. But no one spies as invasively as the NSA. The invasive capabilities we justifiably develop and use for national security shouldn’t be turned to gaining diplomatic or commercial advantage.
And yes, these rows wouldn’t be taking place except for the leaks by Edward Snowden. But it would be unwise for the United States, in today’s interconnected world, to assume that the agency it assigns to steal the secrets of others will be able to perfectly protect its own.
Microsoft outlines 66,539 account requests from law enforcement during first half of 2013
By Timothy J. Seppala posted Sep 28th, 2013 at 11:53 AM 18
We've covered various transparency reports before, but now the whole notion takes on a different feel in our post-PRISM world. Microsoft's latest report details that it received 37,196 requests from law enforcement agencies between this January and June, which impacted 66,539 of its accounts. Seventy-seven percent of those requests were for data like a user's name, IP history and billing address, and with 21 percent of requests, no data was disclosed at all. However, in 2.19 percent of queries by law enforcement, Redmond disclosed "at least some" customer content. What does that mean? Well, the company's definition includes the subject or body of an email, photos stored in SkyDrive and address book info. According to the document, the info was all obtained via lawful warrants and court orders.
While National Security Letters also fall under the guise of law enforcement requests -- which primarily come from the FBI in order to obtain records such as phone numbers and email addresses -- Microsoft is only allowed to publish these statistics on an annual basis. Hence, they're absent this time around, and will be published in the company's next Law Enforcement Requests Report. To see just how deep the rabbit hole goes, do check out the source. We suggest putting on a pot of coffee, though -- it's not a quick read.
NSA watchdog: Employees spied on lovers
Associated Press Fri Sep 27, 2013 10:44 AM
WASHINGTON — Some workers at the National Security Agency intentionally misused the government’s secret surveillance systems at least 12 times over the past decade, including instances when they spied on spouses, boyfriends or girlfriends, according to embarrassing new details disclosed by the agency’s inspector general. In nearly every case, the workers were allowed to retire before they could be punished. [While us civilians will get draconian prison sentences for trivial crimes, government employees rarely get more then a slap on the wrist for major crimes]
In addition to the 12 historical cases, authorities are investigating two other suspected violations and reviewing a third allegation for possible investigation, the inspector general, George Ellard, told Sen. Charles Grassley, R-Iowa, in a letter released late Thursday.
Senior national security officials and some U.S. lawmakers have said such cases were exceedingly rare considering the breadth of the NSA’s surveillance programs and reflect how seriously the government monitors use of its systems for potential abuses. [Yea, that's what they always say. The f*ck up never happened before and will never happen again!!!]
“Where (a media report) says we’re sweeping up the communications of civilians overseas that aren’t targets of collection systems is wrong,” the NSA’s director, Army Gen. Keith Alexander, told senators Thursday. “If our folks do that, we hold them accountable.”
At least six times the cases were reported to the Justice Department for possible prosecution, Ellard’s letter said. In some cases, U.S. prosecutors declined to take action but in nearly every case the employees were allowed to retire without punishment. [Yea, that's what usually happens - nothing] In one case, a worker was suspended without pay then retired; in another case, a worker’s promotion was cancelled; in two cases, military employees suffered a reduction in rank, extra duty and brief reduction in salary for two months.
Public concerns about how telephone and Internet surveillance data is handled by the NSA have intensified in the wake of leaks about the agency’s programs by former contract employee Edward Snowden. With the Senate readying to consider new limits on the NSA’s spying programs, national security officials have sought to boost confidence in their procedures. Senior officials have said they moved quickly to report and correct internal problems that led to the NSA’s accidental collection of 56,000 emails and other communications by Americans, and they insisted that willful abuse of surveillance data by officials is almost non-existent.
Grassley, who had asked Ellard last month to provide more information about the 12 violations, urged robust oversight of the secret programs. “We shouldn’t tolerate even one misuse of this program,” he said. [But our government masters will pretty much tolerate any all all crimes committed by the goons in the NSA]
Several cases clearly showed government officials using the surveillance system to probe for information about spouses or paramours. During a 2011 polygraph test, an official acknowledged tapping into surveillance data about his foreign girlfriend’s telephone number in 2004. The official also tried to retrieve data about his own phone but was prevented because internal mechanisms prevented queries on domestic phone numbers without authorization. The matter was referred to the Justice Department. The official retired in 2012 before internal disciplinary action could be taken.
In another case, the foreign girlfriend of a U.S official reported her suspicions that the official was listening to her telephone calls. An internal investigation found that the official had made internal surveillance queries on the phones of nine foreign women without authorization and had at times listened in on some phone conversations. The same official also collected data on a U.S. person’s phone.
The case was referred to prosecutors and the official resigned before internal discipline could be imposed.
Ex-EPA official pleads guilty to theft; he also had claimed to work for CIA
By Ann E. Marimow and Lenny Bernstein, Published: September 27
A former high-level official at the Environmental Protection Agency admitted Friday that he stole nearly $900,000 from the government by pretending to work for the CIA in a plea agreement that raised questions about how top agency managers failed to detect the scheme since it began in 1994.
John C. Beale duped a series of supervisors, including top officials of the EPA’s Office of Air and Radiation, disappearing from the office and explaining his absences by telling his bosses that he was doing top-secret work for the CIA and its “directorate of operations.”
He lied about contracting malaria (he didn’t) while he served in Vietnam (all his military service was in the United States) to obtain a parking space reserved for the disabled that cost the EPA $8,000 over three years. He took personal trips to Los Angeles for which he charged the government more than $57,000, according to new court filings.
In all, Beale was paid for 21 / 2 years of work he did not perform since early 2000 and received about $500,000 in “retention bonuses” he did not deserve for nearly two decades, according to court papers and interviews.
“To our knowledge, prior to [current EPA Administrator] Gina McCarthy expressing her concerns, no one at EPA ever checked to see if Mr. Beale worked for the CIA,” said Assistant Inspector General Patrick Sullivan, who led the investigation that included interviews of 40 people. Only one, an executive assistant, suspected Beale’s story of working for the clandestine service.
Nor did EPA personnel compare Beale’s travel vouchers, which said he was in places such as Boston and Seattle, with hotel receipts for the same dates that showed him in Bakersfield, Calif., where he has family.
Even during the probe, which began in March, Beale continued to insist that he could not be interviewed because of his work for the CIA, Sullivan said. Only when investigators offered to question him in a secure room at the agency’s Langley headquarters did he admit he had no connection to the CIA, Sullivan said.
For reasons the EPA cannot explain, Beale continued to draw a paycheck until April 30, 19 months after his retirement dinner cruise on the Potomac River and 23 months after he announced he would retire, according to Sullivan and court documents. Beale and his attorney declined to comment after the federal court hearing Friday.
The case has attracted political attention, in part because Beale was defrauding the agency when he worked for McCarthy, the new EPA administrator, when she headed the agency’s Air and Radiation office.
McCarthy started her job in 2009 and told investigators she began to suspect Beale in March 2012, Sullivan said. McCarthy, who is identified as “EPA Manager #2,” in court documents, eventually discovered that Beale was still receiving a paycheck long after she helped celebrate his retirement. She became EPA administrator this year.
McCarthy referred the matter to the EPA general counsel’s office. Instead of being transferred to the inspector general, it was referred to the EPA’s Office of Homeland Security, which has no investigative authority. That delayed the IG’s probe for months, said people familiar with the investigation.
Repeated calls and e-mails to EPA representatives were not returned Friday.
The top Republican on the Senate Environment and Public Works Committee, David Vitter (La.), said Friday that the case highlights a “major failing within EPA” and that “no direct actions have been taken to guarantee this kind of abuse won’t happen again.”
The committee’s chairman, Barbara Boxer (D-Calif.) called Beale’s actions “outrageous” and praised the inspector general and McCarthy for “putting an end to his thievery.” Boxer has scheduled a briefing for Monday. Beale is scheduled to appear at a House Committee on Oversight and Government Reform hearing next week titled “Secret Agent Man?”
Beale, 64, was charged in August with stealing $886,186 in pay and bonuses. A senior policy adviser in the Air and Radiation office, he earned $164,700 when he retired in April. He has repaid the $886,186 to the EPA as part of his plea agreement but still owes a money judgment of $507,000. Beale, who until recently lived in Arlington County, faces up to three years in prison under federal sentencing guidelines.
Even though court documents trace Beale’s conduct to 2000, the IG’s office found that Beale’s deception began in 1989, when he falsely wrote on his employment application that he had worked for former senator John Tunney of California, Sullivan said. Tunney’s name was misspelled on the form, he said. Beale said he began the CIA ruse in 1994, Sullivan said, because he missed the limelight from his work on the Clean Air Act reauthorization from 1990 to 1993.
Early on at the EPA, Beale’s air-quality expertise led to many legitimate overseas trips to places such as China, South Africa and England, said people familiar with the case. His frequent international travel also allowed him to cultivate an aura of mystery, his former colleagues said.
When Beale started disappearing from the office in 2001, he told a person identified as “EPA manager #1” that he was assigned to a special advisory group working on a project with the Directorate of Operations at the CIA, according the court filing.
The manager agreed to Beale’s request to be out of the office one day a week for the CIA work, according to the statement of the offense.
In 2005, court documents say the same manager approved a long-term research project that Beale had proposed. Beale took five trips to Los Angeles to work on the project, which prosecutors said did not require travel. Beale stayed in Bakersfield and visited nearby family members. He was reimbursed more than $57,000 in travel expenses for work that was never produced.
The inspector general’s office identified “manager #1” as Jeffrey R. Holmstead, who was head of the Office of Air and Radiation from 2001 to 2005, during the administration of George W. Bush. Holmstead, a lawyer in Washington, said in an e-mail that he had “no recollection of approving [Beale’s] requests.”
“He did tell me that he had an assignment with the CIA that would sometimes take him out of the office, but I was never asked to approve this arrangement. Career employees are sometimes detailed to work at other agencies, and I assumed that Mr. Beale’s work at the CIA was done pursuant to such an arrangement.”
In 2008, Beale did not show up at the office for about six months, telling his managers that he was either working on a research project or for “Langley,” a reference to the CIA.
Throughout the scheme, Beale was receiving a 25 percent retention bonus that should have expired after three years, in 2003. Instead, he continued to receive the bonus through 2013, according to the court documents, and was among the highest paid, nonelected federal government employees. A close friend of Beale’s, his supervisor Robert Brenner, put him in for the bonus twice, Sullivan said.
In May 2011, Beale announced his retirement. The next month, he told McCarthy that his CIA work would keep him out of the office for long periods. Beale sent e-mails to McCarthy and others at the EPA during that time, saying he was traveling overseas and doing CIA work. In reality, Beale was at home or at his vacation house on Cape Cod, according to the plea agreement.
N.S.A. Gathers Data on Social Connections of U.S. Citizens
By JAMES RISEN and LAURA POITRAS
Published: September 28, 2013 58 Comments
WASHINGTON — Since 2010, the National Security Agency has been exploiting its huge collections of data to create sophisticated graphs of some Americans’ social connections that can identify their associates, their locations at certain times, their traveling companions and other personal information, according to newly disclosed documents and interviews with officials.
The spy agency began allowing the analysis of phone call and e-mail logs in November 2010 to examine Americans’ networks of associations for foreign intelligence purposes after N.S.A. officials lifted restrictions on the practice, according to documents provided by Edward J. Snowden, the former N.S.A. contractor.
The policy shift was intended to help the agency “discover and track” connections between intelligence targets overseas and people in the United States, according to an N.S.A. memorandum from January 2011. The agency was authorized to conduct “large-scale graph analysis on very large sets of communications metadata without having to check foreignness” of every e-mail address, phone number or other identifier, the document said. Because of concerns about infringing on the privacy of American citizens, the computer analysis of such data had previously been permitted only for foreigners.
The agency can augment the communications data with material from public, commercial and other sources, including bank codes, insurance information, Facebook profiles, passenger manifests, voter registration rolls and GPS location information, as well as property records and unspecified tax data, according to the documents. They do not indicate any restrictions on the use of such “enrichment” data, and several former senior Obama administration officials said the agency drew on it for both Americans and foreigners.
N.S.A. officials declined to say how many Americans have been caught up in the effort, including people involved in no wrongdoing. The documents do not describe what has resulted from the scrutiny, which links phone numbers and e-mails in a “contact chain” tied directly or indirectly to a person or organization overseas that is of foreign intelligence interest.
The new disclosures add to the growing body of knowledge in recent months about the N.S.A.’s access to and use of private information concerning Americans, prompting lawmakers in Washington to call for reining in the agency and President Obama to order an examination of its surveillance policies. Almost everything about the agency’s operations is hidden, and the decision to revise the limits concerning Americans was made in secret, without review by the nation’s intelligence court or any public debate. As far back as 2006, a Justice Department memo warned of the potential for the “misuse” of such information without adequate safeguards.
An agency spokeswoman, asked about the analyses of Americans’ data, said, “All data queries must include a foreign intelligence justification, period.”
“All of N.S.A.’s work has a foreign intelligence purpose,” the spokeswoman added. “Our activities are centered on counterterrorism, counterproliferation and cybersecurity.”
The legal underpinning of the policy change, she said, was a 1979 Supreme Court ruling that Americans could have no expectation of privacy about what numbers they had called. Based on that ruling, the Justice Department and the Pentagon decided that it was permissible to create contact chains using Americans’ “metadata,” which includes the timing, location and other details of calls and e-mails, but not their content. The agency is not required to seek warrants for the analyses from the Foreign Intelligence Surveillance Court.
N.S.A. officials declined to identify which phone and e-mail databases are used to create the social network diagrams, and the documents provided by Mr. Snowden do not specify them. The agency did say that the large database of Americans’ domestic phone call records, which was revealed by Mr. Snowden in June and caused bipartisan alarm in Washington, was excluded. (N.S.A. officials have previously acknowledged that the agency has done limited analysis in that database, collected under provisions of the Patriot Act, exclusively for people who might be linked to terrorism suspects.)
But the agency has multiple collection programs and databases, the former officials said, adding that the social networking analyses relied on both domestic and international metadata. They spoke only on the condition of anonymity because the information was classified.
The concerns in the United States since Mr. Snowden’s revelations have largely focused on the scope of the agency’s collection of the private data of Americans and the potential for abuse. But the new documents provide a rare window into what the N.S.A. actually does with the information it gathers.
A series of agency PowerPoint presentations and memos describe how the N.S.A. has been able to develop software and other tools — one document cited a new generation of programs that “revolutionize” data collection and analysis — to unlock as many secrets about individuals as possible.
The spy agency, led by Gen. Keith B. Alexander, an unabashed advocate for more weapons in the hunt for information about the nation’s adversaries, clearly views its collections of metadata as one of its most powerful resources. N.S.A. analysts can exploit that information to develop a portrait of an individual, one that is perhaps more complete and predictive of behavior than could be obtained by listening to phone conversations or reading e-mails, experts say.
Phone and e-mail logs, for example, allow analysts to identify people’s friends and associates, detect where they were at a certain time, acquire clues to religious or political affiliations, and pick up sensitive information like regular calls to a psychiatrist’s office, late-night messages to an extramarital partner or exchanges with a fellow plotter.
“Metadata can be very revealing,” said Orin S. Kerr, a law professor at George Washington University. “Knowing things like the number someone just dialed or the location of the person’s cellphone is going to allow to assemble a picture of what someone is up to. It’s the digital equivalent of tailing a suspect.”
The N.S.A. had been pushing for more than a decade to obtain the rule change allowing the analysis of Americans’ phone and e-mail data. Intelligence officials had been frustrated that they had to stop when a contact chain hit a telephone number or e-mail address believed to be used by an American, even though it might yield valuable intelligence primarily concerning a foreigner who was overseas, according to documents previously disclosed by Mr. Snowden. N.S.A. officials also wanted to employ the agency’s advanced computer analysis tools to sift through its huge databases with much greater efficiency.
The agency had asked for the new power as early as 1999, the documents show, but had been initially rebuffed because it was not permitted under rules of the Foreign Intelligence Surveillance Court that were intended to protect the privacy of Americans.
A 2009 draft of an N.S.A. inspector general’s report suggests that contact chaining and analysis may have been done on Americans’ communications data under the Bush administration’s program of wiretapping without warrants, which began after the Sept. 11 attacks to detect terrorist activities and skirted the existing laws governing electronic surveillance.
In 2006, months after the wiretapping program was disclosed by The New York Times, the N.S.A.’s acting general counsel wrote a letter to a senior Justice Department official, which was also leaked by Mr. Snowden, formally asking for permission to perform the analysis on American phone and e-mail data. A Justice Department memo to the attorney general noted that the “misuse” of such information “could raise serious concerns,” and said the N.S.A. promised to impose safeguards, including regular audits, on the metadata program. In 2008, the Bush administration gave its approval.
A new policy that year, detailed in “Defense Supplemental Procedures Governing Communications Metadata Analysis,” authorized by Defense Secretary Robert M. Gates and Attorney General Michael B. Mukasey, said that since the Supreme Court had ruled that metadata was not constitutionally protected, N.S.A. analysts could use such information “without regard to the nationality or location of the communicants,” according to an internal N.S.A. description of the policy.
After that decision, which was previously reported by The Guardian, the N.S.A. performed the social network graphing in a pilot project for 1 ½ years “to great benefit,” according to the 2011 memo. It was put in place in November 2010 in “Sigint Management Directive 424” (sigint refers to signals intelligence).
In the 2011 memo explaining the shift, N.S.A. analysts were told that they could trace the contacts of Americans as long as they cited a foreign intelligence justification. That could include anything from ties to terrorism, weapons proliferation, international drug smuggling or espionage to conversations with a foreign diplomat or a political figure.
Analysts were warned to follow existing “minimization rules,” which prohibit the N.S.A. from sharing with other agencies names and other details of Americans whose communications are collected, unless they are necessary to understand foreign intelligence reports or there is evidence of a crime. The agency is required to obtain a warrant from the intelligence court to target a “U.S. person” — a citizen or legal resident — for actual eavesdropping.
The N.S.A. documents show that one of the main tools used for chaining phone numbers and e-mail addresses has the code name Mainway. It is a repository into which vast amounts of data flow daily from the agency’s fiber-optic cables, corporate partners and foreign computer networks that have been hacked.
The documents show that significant amounts of information from the United States go into Mainway. An internal N.S.A. bulletin, for example, noted that in 2011 Mainway was taking in 700 million phone records per day. In August 2011, it began receiving an additional 1.1 billion cellphone records daily from an unnamed American service provider under Section 702 of the 2008 FISA Amendments Act, which allows for the collection of the data of Americans if at least one end of the communication is believed to be foreign.
The overall volume of metadata collected by the N.S.A. is reflected in the agency’s secret 2013 budget request to Congress. The budget document, disclosed by Mr. Snowden, shows that the agency is pouring money and manpower into creating a metadata repository capable of taking in 20 billion “record events” daily and making them available to N.S.A. analysts within 60 minutes.
The spending includes support for the “Enterprise Knowledge System,” which has a $394 million multiyear budget and is designed to “rapidly discover and correlate complex relationships and patterns across diverse data sources on a massive scale,” according to a 2008 document. The data is automatically computed to speed queries and discover new targets for surveillance.
A top-secret document titled “Better Person Centric Analysis” describes how the agency looks for 94 “entity types,” including phone numbers, e-mail addresses and IP addresses. In addition, the N.S.A. correlates 164 “relationship types” to build social networks and what the agency calls “community of interest” profiles, using queries like “travelsWith, hasFather, sentForumMessage, employs.”
A 2009 PowerPoint presentation provided more examples of data sources available in the “enrichment” process, including location-based services like GPS and TomTom, online social networks, billing records and bank codes for transactions in the United States and overseas.
At a Senate Intelligence Committee hearing on Thursday, General Alexander was asked if the agency ever collected or planned to collect bulk records about Americans’ locations based on cellphone tower data. He replied that it was not doing so as part of the call log program authorized by the Patriot Act, but said a fuller response would be classified.
If the N.S.A. does not immediately use the phone and e-mail logging data of an American, it can be stored for later use, at least under certain circumstances, according to several documents.
One 2011 memo, for example, said that after a court ruling narrowed the scope of the agency’s collection, the data in question was “being buffered for possible ingest” later. A year earlier, an internal briefing paper from the N.S.A. Office of Legal Counsel showed that the agency was allowed to collect and retain raw traffic, which includes both metadata and content, about “U.S. persons” for up to five years online and for an additional 10 years offline for “historical searches.”
James Risen reported from Washington and New York. Laura Poitras, a freelance journalist, reported from Berlin.
John McAfee reveals details on gadget to thwart NSA
By Tracey Kaplan
tkaplan@mercurynews.com
Posted: 09/28/2013 07:06:58 PM PDT
SAN JOSE -- John McAfee lived up to his reputation Saturday as tech's most popular wild child, electrifying an audience with new details of his plan to thwart the NSA's surveillance of ordinary Americans with an inexpensive, pocket-size gadget.
Dubbed "Decentral," the as-yet-unbuilt device will cost less than $100, McAfee promised the enthusiastic crowd of about 300 engineers, musicians and artists at the San Jose McEnery Convention Center.
"There will be no way (for the government) to tell who you are or where you are," he said in an onstage interview with moderator Dan Holden at the inaugural C2SV Technology Conference + Music Festival.
And if the U.S. government bans its sale, "I'll sell it in England, Japan, the Third World. This is coming and cannot be stopped."
The ambitious -- some would say quixotic -- project is the latest chapter of McAfee's colorful life.
The anti-virus software pioneer's antics have included his widely publicized flight last year from Belize, where he remains wanted as a "person of interest" in the shooting death of his neighbor.
Even so, he remains an icon in the annals of Silicon Valley's history of entrepreneurship. In 1989, he founded the anti-virus software company that still bears his name and once was worth $100 million. In 1994, he ended his relationship with the company and moved to Colorado.
During the interview, the 68-year-old with spiky black hair tipped blond, who wore light blue cargo pants and a black sweatshirt, remarked on a wide range of topics, from how quickly he gets bored once one of his creations comes to fruition (including the software security company he founded) to how yoga helped him 30 years ago to quit using drugs, including his favorite (psychedelic mushrooms).
It was a talk bound to appeal to the young audience, which broke into frequent applause. Among the group was his new 30-year-old wife, Janice Dyson. She said in a brief interview
afterward with this newspaper that she is a former stripper. The couple met in Miami, where McAfee went after being deported from Guatemala.
"I keep him grounded," she said.
McAfee outlined what some might regard as a pie-in-the-sky plan to finish the first prototype of the Decentral in six months. He said the gadget is called Decentral because by communicating with smartphones, tablets and other devices, it will create decentralized, floating and moving local networks that can't be penetrated by government spy agencies.
The design is in place already for a version whose range will be three blocks in the city and a quarter mile in the country, he said. The device will be compatible with both Android and iPhones.
As far as consumers' appetite for such a gizmo, he said, "I cannot imagine one college student in the world who will not stand in line to get one."
Commuters will also find it useful, he said. Neighborhoods will be better able to fight crime because Decentral will include an option that sends an alert if there is a burglary or other crime.
McAfee said the idea for the device came to him well before computer analyst and whistleblower Edward Snowden leaked National Security Agency documents that exposed widespread monitoring of U.S. citizens' phone calls and Internet communications.
But with Snowden's actions, "it became the right time" to make it real, he said.
At the end of the 75-minute discussion, McAfee gamely took questions from the audience about everything from what advice he'd give teens (do what you love) to what he fears (his wife, he joked). In response to a question about marijuana, he made clear he doesn't embrace every aspect of the youth culture.
He said he liked pot users when he sold drugs decades ago because their "lives never go anywhere and they remain customers," adding, "Marijuana is a drug of illusion -- it creates the illusion that you're doing great things when all you're doing is sitting on the sofa growing a beard."
McAfee also reiterated that he never killed anyone in Belize and fled after angering the authorities by refusing to pay a $2 million bribe.
There seemed to be intense interest Saturday in McAfee's
John McAfee, right, speaks with Dan Holden at the "Fireside Chat with John McAfee" during the C2SV Technology Conference + Music Festival at the McEnery Convention Center in San Jose, Calif., on Saturday, Sept. 28, 2013. (LiPo Ching/Bay Area News Group) ( LiPo Ching )
current plans. One man asked whether Decentral essentially creates a "dark Web," or part of the Internet that can no longer be accessed by conventional means.
Yes, he said.
Will the privacy it affords allow criminals and others to evade the authorities, another wanted to know.
"It will of course be used for nefarious purposes," he said, "just like the telephone is."
Contact Tracey Kaplan at 408-278-3482.
Vice Admiral Is Suspended in Gambling Investigation
By MICHAEL SCHWIRTZ and RAVI SOMAIYA
Published: September 28, 2013
A vice admiral who is second in command at the United States Strategic Command, which oversees nuclear war-fighting forces for the military, has been suspended amid an investigation into his possible involvement in illegal gambling, officials said on Saturday.
The officer, Vice Adm. Timothy M. Giardina, is a highly decorated sailor with more than three decades in the Navy. The suspension occurred on Sept. 3, but was not announced publicly, said Capt. Pamela Kunze, the command’s spokeswoman.
Captain Kunze would not comment further on the circumstances surrounding the suspension, citing a continuing investigation by the Naval Criminal Investigative Service.
The Strategic Command was first alerted about the issue in mid-July. A month earlier, Admiral Giardina became the target of an inquiry being conducted by the Iowa Division of Criminal Investigation into possible use of counterfeit gambling chips at the Horseshoe Casino in Council Bluffs, Iowa, said David Dales, the head of the Southwest division of the Iowa Division of Criminal Investigation.
Mr. Dales said the criminality in question involved poker at the casino, but said he could provide no further information. The agency’s investigation is still open and no state charges have been filed against Admiral Giardina, Mr. Dales said.
It was not clear whether Admiral Giardina’s actions compromised national security or the operations of the Strategic Command.
The commander of the Strategic Command, General C. Robert Kehler, has submitted a recommendation to Defense Secretary Chuck Hagel that Admiral Giardina be reassigned, Captain Kunze said. It has not been determined what, if any, additional actions will be taken. The leadership of the Strategic Command is appointed by the president and confirmed by the Senate.
The Strategic Command, based at Offutt Air Force Base near Omaha, oversees a web of military efforts including the military’s space and cyberwarfare operations. It also controls the country’s nuclear arsenal.
Admiral Giardina, a career submarine officer, assumed his duties at the Strategic Command in December 2011. Before that, he was the deputy commander and chief of staff of the Pacific Fleet. He graduated from the Naval Academy in 1979.
He was scheduled to rotate out of his position at Strategic Command later this year. In early July, President Obama appointed an Air Force general to replace Admiral Giardina.
Tim Giardina Suspended: No. 2 U.S. Nuke Commander Under Investigation
By ROBERT BURNS 09/28/13 06:10 PM ET EDT AP
WASHINGTON — The No. 2 officer at the military command in charge of all U.S. nuclear war-fighting forces is suspected in a case involving counterfeit gambling chips at a western Iowa casino and has been suspended from his duties, officials said.
Navy Vice Adm. Tim Giardina has not been arrested or charged, Iowa Division of Criminal Investigation special agent David Dales said Saturday. The state investigation is ongoing.
Giardina, deputy commander at U.S. Strategic Command, was suspended on Sept. 3 and is under investigation by the Naval Criminal Investigative Service, a Strategic Command spokeswoman said.
The highly unusual action against a high-ranking officer at Strategic Command was made more than three weeks ago but not publicly announced at that time. The command is located at Offutt Air Force Base near Omaha, Neb.
Air Force Gen. Robert Kehler, who heads Strategic Command, suspended Giardina, according to the command's top spokeswoman, Navy Capt. Pamela Kunze. Giardina is still assigned to the command but is prohibited from performing duties related to nuclear weapons and other issues requiring a security clearance, she said.
Kehler has recommended to Defense Secretary Chuck Hagel that Giardina be reassigned, Kunze said. Giardina has been the deputy commander of Strategic Command since December 2011. He is a career submarine officer and prior to starting his assignment there was the deputy commander and chief of staff at U.S. Pacific Fleet.
DCI agents stationed at the Horseshoe Casino in Council Bluffs, Iowa, discovered the counterfeit chips, Dales said. He would not say when the discovery was made or how much in counterfeit chips was found, only that "it was a significant monetary amount."
Council Bluffs is located across the Missouri River from Omaha.
"We were able to detect this one pretty quickly and jump on it," Dales said. He declined to give specifics on how authorities determined that casino chips had been counterfeited or how Giardina might have been involved.
Strategic Command oversees the military's nuclear fighter units, including the Navy's nuclear-armed submarines and the Air Force's nuclear bombers and nuclear land-based missiles.
Kunze said Strategic Command did not announce the suspension because Giardina remains under investigation and action on Kehler's recommendation that Giardina be reassigned is pending. The suspension was first reported by the Omaha World-Herald.
Kunze said a law enforcement investigation of Giardina began June 16. Kehler became aware of this on July 16, and the following day he asked the Naval Criminal Investigative Service to begin a probe.
The suspension is yet another blow to the military's nuclear establishment. Last spring the nuclear missile unit at Minot Air Force Base, N.D., pulled 17 launch control officers off duty after a problematic inspection and later relieved of duty the officer in charge of training and proficiency.
In August a nuclear missile unit at Malmstrom Air Force Base, Mont., failed a nuclear safety and security inspection; nine days later an officer in charge of the unit's security forces was relieved of duty.
___
Associated Press writer Margery A. Beck in Omaha, Neb., contributed to this report.
Previous
articles
on
Edward Snowden NSA Freedom Fighter!!!
More
articles
on
Edward Snowden NSA Freedom Fighter!!!
Put NSA in a narrower box
Robb should be writing that the criminals in the NSA who violated our 4th Amendment rights should be put in prison. Same goes for the members of the US Senate and US House who supported the unconstitutional Patriot Act which is just an end run around the 4th Amendment.
Microsoft outlines 66,539 account requests from law enforcement
No, I am not paranoid - the government IS SPYING ON YOU!!!!!
NSA watchdog: Employees spied on lovers
Source
Ex-EPA official pleads guilty to stealing $900K
Source
N.S.A. Gathers Data on Social Connections of U.S. Citizens
I drive a foreign made Volkswagen and eat lots of Mexican food. I suspect that is justification for the goons at the NSA to spy on me. At least with the convoluted, cockamamie logic the NSA uses to justify flushing the 4th Amendment down the toilet and spying on Americans.
John McAfee reveals details on gadget to thwart NSA
John McAfee seems to be able to shovel the BS as well as any professional politician does so I am not sure if this is something that is real or if
John McAfee just wants to remove some money from your wallet.
No. 2 U.S. Nuke Commander Under Investigation
Admiral Giardina is being investigated for using counterfeit gambling chips at the Horseshoe Casino